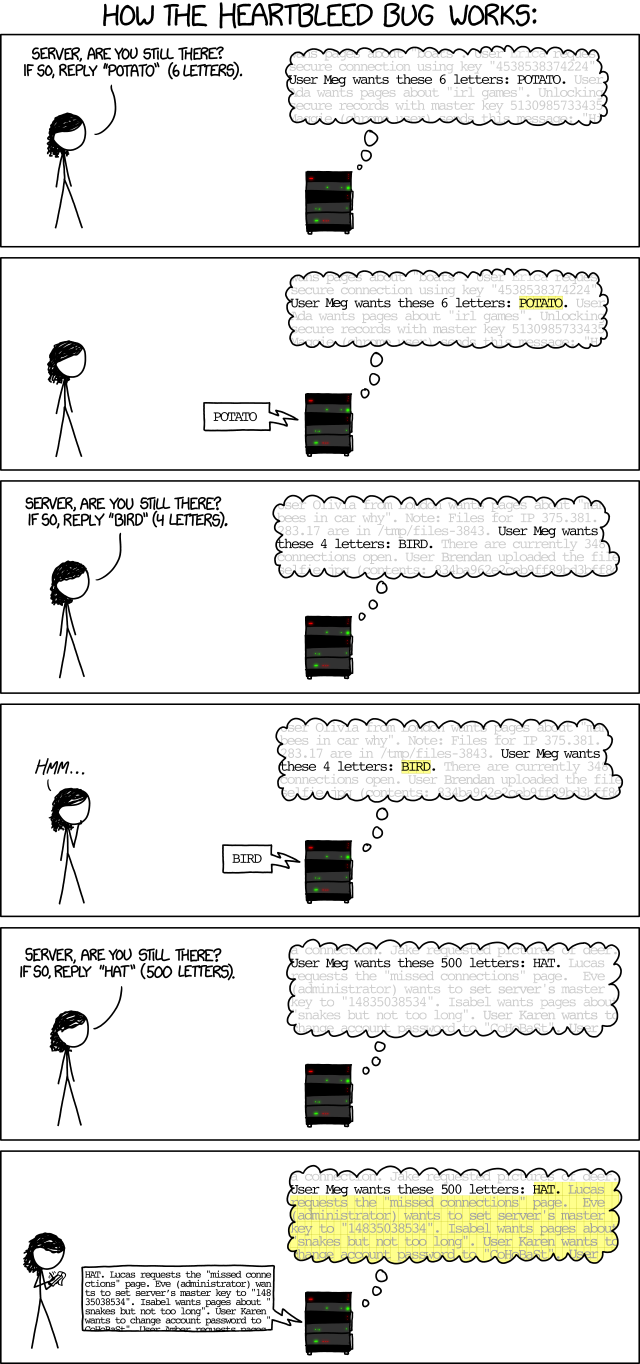
There is a serious security vulnerability that has possibility of affecting most banking and shopping sites. It's called the heartbleed bug. Here's a link to what CNET has to say, 'Heartbleed' bug undoes Web encryption, reveals Yahoo passwords - CNET
I would suggest that everyone postpone online shopping and banking for at least a day or two. My bank assures me that they aren't vulnerable because they care about security and use SSL. Not convincing - the bug is in SSL.
I wish PayPal, and banking sites would post something about this on their landing page. Revenue Canada did. They have temporarily closed netfile, efile, etc., etc.
I would suggest that everyone postpone online shopping and banking for at least a day or two. My bank assures me that they aren't vulnerable because they care about security and use SSL. Not convincing - the bug is in SSL.

I wish PayPal, and banking sites would post something about this on their landing page. Revenue Canada did. They have temporarily closed netfile, efile, etc., etc.